Vulnerabilities are a simple fact of life. The goal for vendors and organizations is not to strive to create perfect hardware or software that has no vulnerabilities—there is no such thing. What’s important is ensuring that relevant details and context are shared so there is awareness of any flaws and an opportunity to address or mitigate security concerns. A paper from IDC—“Silicon as Code, the Cybersecurity Vulnerability Paradox, and the Transparency Requirements for a 21st Century Processor Vendor”—takes a closer look at supply chain risk and the importance of transparency.
Why does transparency matter? Organizations need to have visibility and context for the vulnerabilities that exist in the hardware and software they use so they can protect them effectively. It is also important for establishing and maintaining trust between security researchers and vendors, as well as between vendors and customers.
The IDC white paper is sponsored by Intel, which also published its own report on the subject—“The Role of Transparency and Security Assurance in Driving Technology Decision-Making”—earlier this year. Intel is no stranger to the value of transparency and the need for Coordinated Vulnerability Disclosure to ensure that balance is maintained between visibility and security. Information needs to be clearly communicated in a timely manner, but disclosing information publicly too soon actually increases risk.
Rising Rate of CVEs
According to the IDC research, there have been more vulnerabilities discovered and identified in the last five years as there were in the prior 16. 2020 saw a decline in total Common Vulnerabilities and Exposures (CVEs), but that may in part be related to global lockdown efforts in response to the COVID-19 pandemic. There is no reason to assume that rate will not go back up and continue to accelerate as nations get vaccinated and businesses open up and return to normal.
The report also reveals that a typical system reaching end of life today will have seen the disclosure of more than 130,000 CVEs affecting it. The combination of longer PC refresh cycles and dramatically accelerating rates of CVEs disclosed indicates that this number will likely continue to rise.
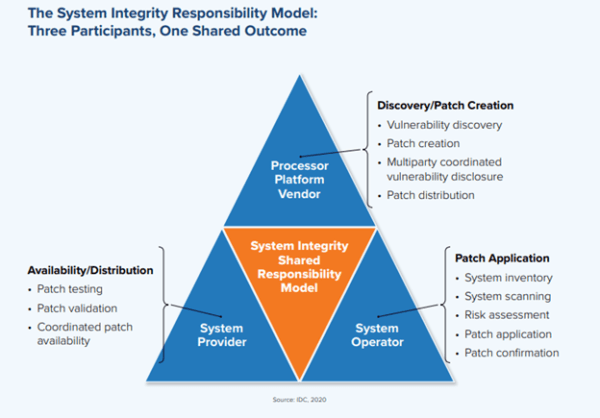
Shared Responsibility Model
It is important for processor platform vendors, system providers, and the customers that use the systems to all cooperate for the most effective protection against vulnerabilities. It is a shared responsibility model where each plays an important role.
- Patch creation — processor platform vendor’s responsibility
- Availability/distribution of patch — system provider’s responsibility
- Application of the patch — system operator’s responsibility
The author of the paper, Frank Dickson, program vice president, Security & Trust at IDC, explains, “Vulnerabilities and their known/unknown status create a cybersecurity paradox. Protecting IT architectures from unknown vulnerabilities is challenging, requiring sophisticated expertise and large resources. Protecting IT architectures from known vulnerabilities is typically more straightforward; the application of a patch is generally considered the greatest return in security.”
Dickson added, “Proactively sharing internal and external research, developer guidance and mitigation methods to ease the system operator’s burden is as critical as enabling application of the patch. Keys to creating system trust are visibility and transparency.”
Dickson sums up the paper with, “Vulnerabilities are not malignant by default; they are simply an uncomfortable reality to be addressed. Vulnerabilities don’t become malignant until they are maliciously and nefariously exploited. Persistent and aggressive patching can help prevent exploitation and encourages profit-maximizing cybermiscreants to attack other targets.”
The most important takeaway from the paper in my opinion is that the more we proactively share research and relevant information, the better it is for everyone. Transparency and trust are key.
- Navigating Cybersecurity Complexity - July 18, 2025
- AI Voice Clones and Mobile Phishing: The Cyber Threats You’re Not Ready For - July 11, 2025
- Rethinking Cloud Security for the Evolving Threat Landscape - July 11, 2025




Comments are closed.