There’s no shortage of readily available hacker tools and techniques, and stories in the news about mobile app hacks for both the iOS and Android platforms. Fortunately, security solutions providers have responded swiftly and there are many approaches that one can leverage to harden an app that is “out in the wild.”
For those of you who may not be familiar with the term, “hardening” is a key step at the end of any secure software development lifecycle process which:
· Confirms that the app is running as designed at runtime
· Thwarts hackers’ efforts to reverse engineer the app back to source code
Which hardening approach is right for your app? To the uninformed purchaser, simple obfuscators are attractive because they are low in cost, require little training and are quick to implement. However, given the sophistication of today’s hackers, it is important for app developers to look beyond the surface and take a more strategic approach to choosing an application hardening solution.
Below are four key factors that IT Security professionals should consider when evaluating application hardening solutions:
#1: Value of your applications
A key factor to consider is the level of investment your company is making in an app in terms of R&D and maintenance costs.
· If valuable proprietary intellectual property such as algorithms or monetizable content is embedded within the app, you should consider the potential revenue loss to your company if the app is successfully hacked.
· If the app processes sensitive information such as financial transactions, account information or authorization credentials, you should consider the potential loss of revenue through fraud and potential collateral damage that could occur if the app is hacked or Trojanized. Collateral damage may include penalties for non-compliance with regulations, expenditures on security upgrades, and even costs associated with crisis management communication campaigns to manage adverse publicity and restore brand value.
There is a prevalent belief that encryption and basic obfuscation techniques in and of themselves are adequate measures to protect apps against hacking. String encryption and variable renaming form a beneficial security layer, but they are inadequate when used in isolation.
Also, it is important to understand that not all obfuscation and encryption tools are created equal. Obfuscation is often confused with simple method renaming techniques and basic string obfuscation technologies, which can be quickly broken and easily reversed. Further, any encryption wrapper that applies the same measures of protection across all the apps it secures can be easily broken by determined hackers. Remember that once a wrapper technology is broken, every application secured by that vendor will be compromised.
See chart 1 below for recommended protection techniques for Low and High Value apps.
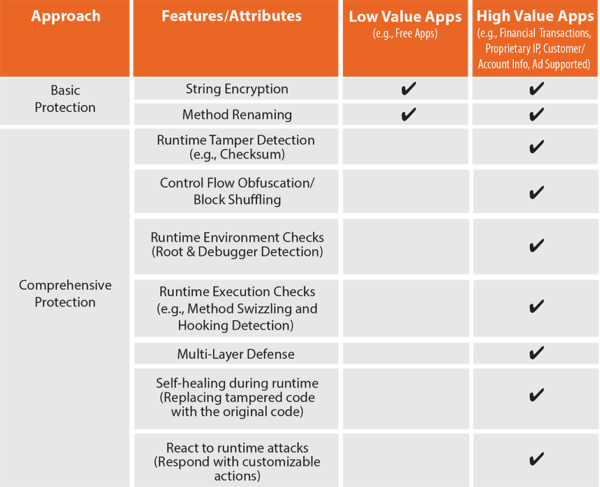
#2: Scale and Sophistication of Attacks Your Apps Will Likely Face
Minimal protections against counterfeiting and repackaging are built into the app distribution ecosystem—including measures such as:
· Detection of jailbreak or root conditions that enable side-loading of applications, many of which are Trojanized.
· Monetization libraries to confirm that only legitimate applications are downloaded through an app store and that they are correctly purchased or licensed. However, these libraries can and are often breached by cybercriminals.
· Audit processes to validate that only legitimate and harmless apps are placed in the app store. Audit mechanisms to block illegitimate apps from distribution to users are far from perfect, as seen by recent iOS malware, including XcodeGhost.
Consequently, it is important to determine the scale and sophistication of attacks that you anticipate for your applications, and validate that the security solution you rely on is capable of meeting the challenge. For small-scale developers with free- or ad-supported apps, typically basic application protection will suffice, even though ad revenue may be subverted through Trojanization.
In contrast, for business-critical enterprise applications, it is safe to assume that an organized army of hackers will be actively looking for ways to subvert your app as quickly and as comprehensively as possible. Since such attacks are designed to be covert, it can take weeks or even months until evidence of a successful hack surfaces. For that reason, measures of defense against attacks have to be complemented by measures of detection and reaction. For example, deeply instrumenting an app to detect attempted attacks and react with functions such as “phone home” can provide long-lasting and durable protection.
Consider the recent benchmarking study that analyzed an Android Java mobile payment application that was hardened with a comprehensive protection solution against the same application with a Basic Java protection solution. Key findings from the study appear in the chart below:
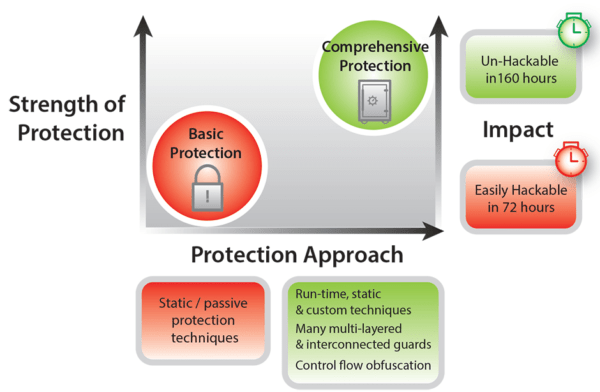
Attacks that systemically compromise the underlying libraries an app relies on are the fastest growing class of attacks—and presently the most dangerous. This makes it imperative that high value apps are able to verify the pristine nature of their entire execution environment before unlocking sensitive functionality. Obfuscation solutions that focus solely on variable renaming or string encryption can deter static reverse engineering but are not able to protect against the full spectrum of high-intensity attempts to compromise the app.
#3: Agility and Portability
The portable device ecosystem, spanning smartphones and tablets and wearable devices, is among the fastest growing and fastest evolving. In stark contrast to the PC ecosystem — which is dominated by only a few chipset and operating system combinations, the portable ecosystem is a combinatorial nightmare of chipsets, OSs, programming technologies and hardware functionality.
Because it is likely that mobile platforms will continue to evolve at their current breakneck and unpredictable pace, choosing a solid security partner with a history of innovation—that can keep pace with evolving ecosystems—is crucial. Additionally, selecting a security tool that is designed for cross-platform portability and extensibility will go a long way in helping you adapt to new platforms that become available.
#4: Overhead and Performance Impact
Memory footprint, power consumption and performance are important considerations in portable devices, where resources are limited and battery life is precious. All security technology will impose an additional memory footprint in storage and at run-time. It will also impose process overhead in terms of programming effort, compilation complexity and run-time execution characteristics.
That said, more sophisticated application hardening solutions can offer a stronger trade-off between performance impact and protection strength relative to free- or low-cost solutions. For example, brute-force simple obfuscation can quickly cause memory bloat and diminish execution speed, while basic check summing can adversely impact run-time performance while retaining single points of protection failure.
When apps are deployed to millions or billions of users, and/or where transaction volumes are expected to be high, it is crucial that the security solution chosen be as robust and reliable as your own app code. Obfuscating sections of the code that are sensitive to performance degradation, such as computation-intensive functions or graphics rendering routines, has an impact on runtime performance. It’s paramount to choose a protection solution that offers tunable performance vs. security tradeoff measures, and provides developers better control on size and performance of their code.
The rise of mobile computing and soaring app usage has companies of every size and caliber scrambling to keep up. With customer loyalty and revenues at stake, developers are scrambling to release cutting-edge apps with little thought for long-term security considerations. In these conditions, it is tempting to treat code hardening as a checkbox and select the cheapest, most readily downloadable tool to do the job – but let the buyer beware. If you take the time to assess the value of your applications and the available options, you’ll realize that if you have a high value app and focus solely on cost, you are likely to be “penny wise and pound foolish.”
- Top 8 actions for runtime application protection - December 3, 2015
- What approach to application hardening is right for your organization? - October 26, 2015




25% of the businesses will be owning their own Enterprise App Stores. So, if your business is running on apps, setting up an Enterprise App Store will be the best thing that you could be doing to your company. Mobility solutions companies mobileapptelligence are developing top apps to keep their clients ahead of the curve.