Since March 29, 2019, Ixia’s Application and Threat Intelligence (ATI) center has been tracking the latest malicious campaign against consumer-grade routers. Today, April 5th, we captured a new wave of attacks that use a different DNS server. The purpose of these attacks is to modify DNS settings in the routers to point to unauthorized webpages that skim user input data. When end users try to access a targeted website, they will land on a webpage designed to look like the original but is controlled by the attacker.
DNS is the backbone of the modern Internet—whenever a user types a domain name in their browser, they expect to be taken to the necessaryserver without having to remember an IP address – DNS attempts to do that. Normally, it should take you to that server and none other. However, a malicious attacker able to intercept your requests could send faked DNS responses pointing you to a malicious server hosting a fake bank login page. That server would then grab your credentials, giving the attacker access to your bank accounts.
A user’s home router is his connection point to the Internet and, generally, does some of the DNS resolution work. As a result, an attacker able to modify DNS settings on a home router will be able to redirect their traffic towards whatever server they want. There is some profit from one target. But multiplying by the number of vulnerable routers that exist out there could bring Big Profit!
Some of the consumer-grade routers targeted:
- D-Link DSL Routers
- DSLink 260E
- ARG-W4 ADSL Router
- Secutech Routers
- TOTOLINK Routers
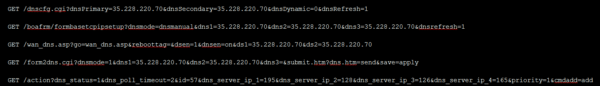
The malicious DNS servers pushed by attackers came in two pairs:
- 195.128.124.150 – primary
- 195.128.124.181 – secondary
and
- 195.128.124.131 – primary
- 195.128.126.165 – secondary
This malicious wave is part of an ongoing DNS hijacking campaign that started as early as December 29, 2018 according to this excellent technical report published by Troy Mursch.
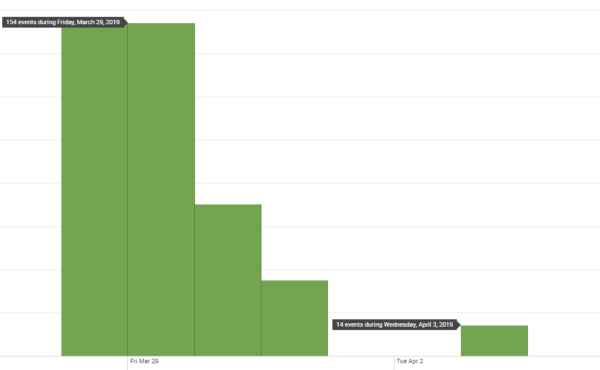
New wave of DNS hijacking identified on 05 April 2019
Today we noticed that new attacks have been caught in our honeypots, this time with a new DNS server (35.228.220.70 – which is set both as primary and secondary DNS server). This time, we managed to catch them in the act – or at the beginning of the act – as you’ll understand later.
We first wanted to dig deeper and understand exactly which domain names were targeted by the attackers. By going through the top 10k domains names provided by Alexa Top 1 Million list and interrogating the malicious servers, we were able to extract a list of websites targeted in this campaign.
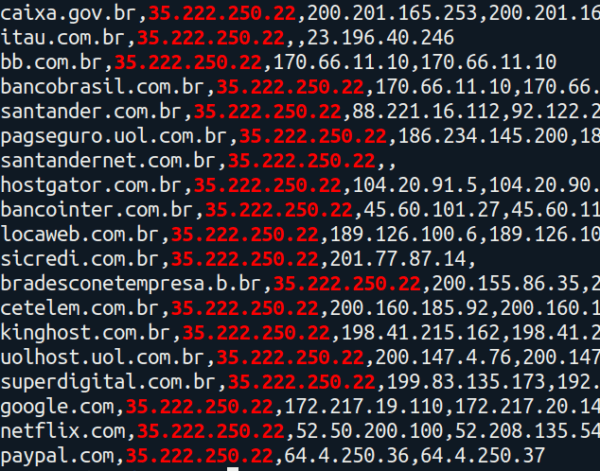
The attackers seem to have three types of targets they are going after. Global Internet-based enterprises, local hosting providers and last, but not least, financial intuitions based in Brazil.
Internet-based global enterprises:
- paypal.com
- gmail.com
- uber.com
- netflix.com
Local web hosting providers:
- hostgator.com.br
- kinghost.com.br
- uolhost.uol.com.br
- locaweb.com.br
Brazilian banks and financial institutions:
- caixa.gov.br
- itau.com.br
- bb.com.br
- sicredi.com.br
- cetelem.com.br
- bancobrasil.com.br
- santander.com.br
- pagseguro.uol.com.br
- santandernet.com.br
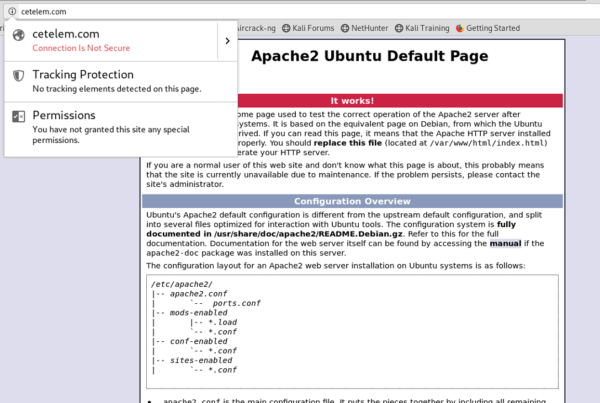
By changing the DNS server and accessing some of the targeted domains, we can see that on the fake page, the webservers are unsecured, running on HTTP instead of HTTPS (which isn’t even running).
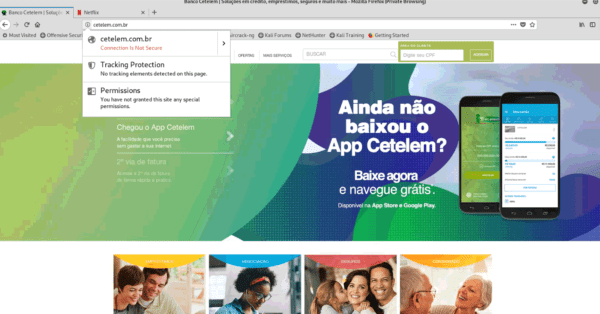
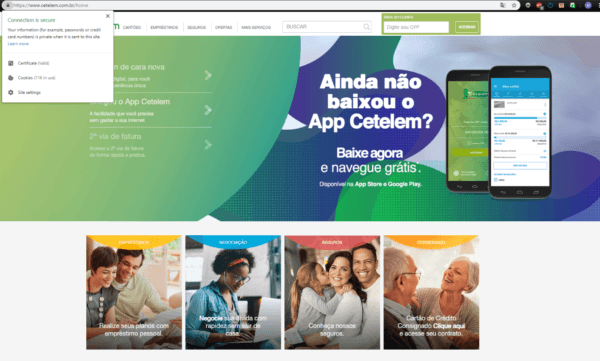
More so, some of the targets aren’t even fully functional yet, which indicates either the attackers haven’t had the time to configure their servers, which is unlikely, considering that the latest DNS change attacks occurred just two days ago (April 3rd), or that the attackers simply misconfigured the Apache configuration.
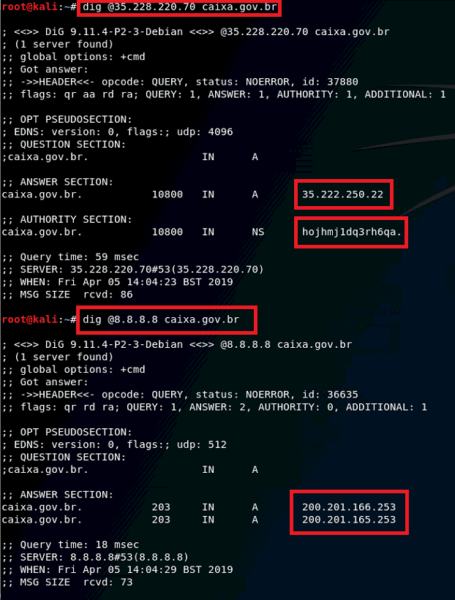
By querying the malicious DNS server for specific domains, we can easily compare the results with queries against Google’s 8.8.8.8 resolver, clearly indicating something is wrong.
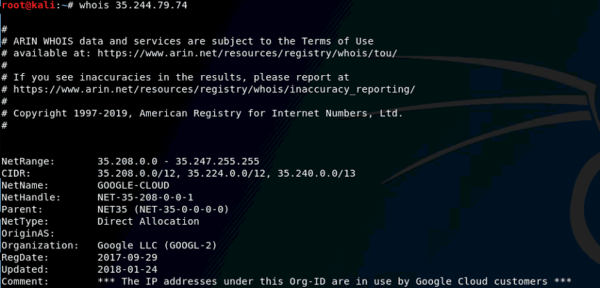
Interestingly, all the attacks captured on April 3rd came from one single IP address 35.244.79.74, which belongs to Google. The attacker’s DNS and Web server is hosted at 35.228.220.70, which also belongs to Google.
It’s 2019 and the Internet is still a dangerous place. However, simple precautions can mitigate many of the risks we face online. Making sure that our devices—in this case routers—are up-to-date and not exposing the admin interface online is important.
Also, be extra careful when accessing important websites, banking especially. Make sure that the connections are HTTPS, check the certificate. All of this is important to make sure that when you’re entering your credentials, they don’t get to someone else.



