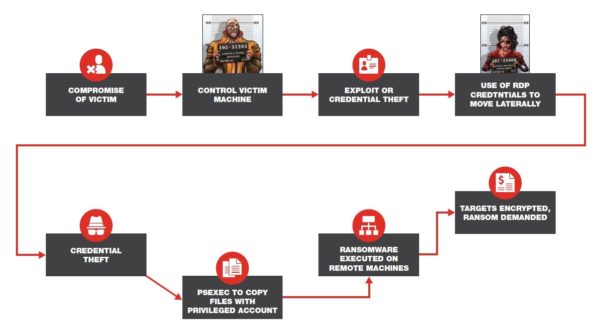
In May 2019, most of Baltimore’s government computer systems were infected with a new and aggressive ransomware variant named RobbinHood. All servers, with the exception of essential services, were taken offline as a result of targeted attacks. In a ransom note, hackers demanded over $75,000 in bitcoin.
A week later, all systems remained down for city employees and a full recovery is still in progress today. It was the second major use of RobbinHood ransomware on an American city in 2019, as Greenville, North Carolina, was also impacted.
The diagram below illustrates the likely attack progression:
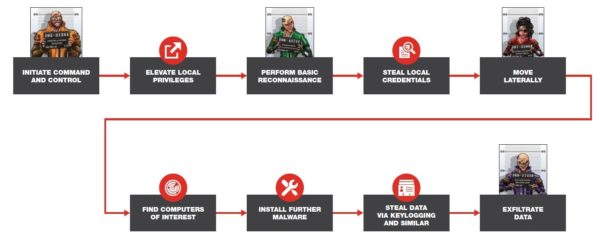
Separately, campaigns typically conducted by an APT group named Thrip have recently emerged. Evidence suggests that the Thrip campaign’s objective is cyber espionage. Targeted industries include defense, telecom and satellite sectors, specifically the geospatial sector.
A potentially disruptive component to this threat was Thrip’s targeting of a satellite communications operator. Once an attack foothold was established, the attackers identified devices that monitor and control satellites and then moved laterally to compromise and own them. The attackers may have wanted to gather intelligence and exfiltrate data, as well as potentially disable the satellites themselves.
The illustration below shows the likely attack progression:
Common themes of targeted attacks
What do these attacks have in common? Both of them targeted and leveraged privileged entities due to the unfettered access they can provide. Escalation from a regular user account to a privileged account is a critical step for the attackers on their way towards their ultimate goal. Privileged entities are not just limited to accounts, but also hosts and services within the network environment.
Hackers can use stolen access privileges to pilfer proprietary digital assets and data without raising alarms, wreak havoc and disruption across the network environment, or subvert your business processes or financial payments. Sadly, that’s just the beginning.
Cyber attackers and security practitioners are aware of this exposure and risk. A recent report from Gartner reveals privileged access as the top priority among security practitioners. Additionally, Forrester estimates that 80 percent of security breaches involve privileged accounts.
Yet, current approaches to security unintentionally leave these entities exposed. Approaches are prevention-oriented or rely on manual entitlements that identify threats the moment they occur, leaving little time to properly respond. Other approaches treat all entities as of equal value and employ pattern-based techniques resulting in excessive volumes of alerts that are impossible to operationalize.
Unfortunately, security teams today lack the ability to quickly and dynamically determine the entities that will be targeted by attackers and anticipate encroachment.
A new approach
Security teams require a new approach. Rather than relying on the granted privilege of an entity or being agnostic to privilege, the approach needs to focus on how entities are actually utilizing their privileges within the network, e.g. observed privilege.
This viewpoint is similar to how attackers observe or infer the interactions between entities. It is imperative that defenders think in a similar fashion to their adversaries. This can occur in two parts:
- Observe the interactions between entities. Based on the behavioral interactions between entities and the sensitivity of assets that are eventually accessed, dynamically determine each entity’s level of privilege. Entities with similar access patterns are grouped as peers. This can be achieved using artificial intelligence and machine learning models.
- Determine abnormalities of interactions between privileged entities. Compare a given access request to the access history to determine distance from normal group distance. Focus on the abnormalities that actually have security implications and consequences.
A standard example is one where all three entities involved in an interaction are privileged and usually have nothing to do with one another. Consider a separate example: A high-privilege account is used from a host it normally operates from to access a service that is not typically used by this account. This would commonly occur when an attacker compromised a host, successfully stole the credential of an account on it, and started to explore all accessible services. Alternatively, this could be a scenario where an administrator has gone rogue.
In the context of the Robbinhood and Thrip examples, such a capability could provide high-fidelity visibility into the most critical part of a targeted attack: The attackers march towards ever more privileged credentials to use in their reconnaissance and lateral movement within the network.



