Qualys is a sponsor of TechSpective
The use of containers and container orchestration platforms like Kubernetes has exploded in recent years. Along with migrating to the cloud and embracing DevOps culture, containers enable significantly greater agility and scalability than traditional applications, and also accelerate the development lifecycle. Like traditional applications, containerized applications need security, but the nature of containers also makes this a more challenging endeavor—especially when trying to protect containers at runtime.
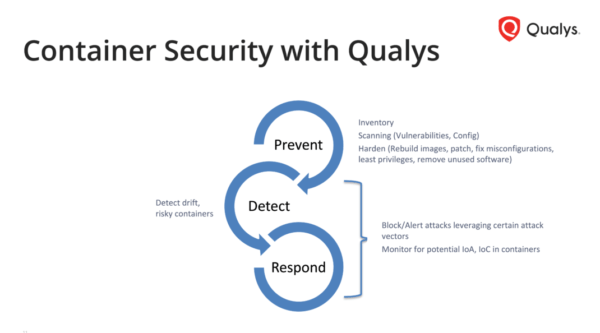
Earlier this month, Qualys announced availability of Container Runtime Security (CRS)—an add-on to Qualys Container Security. The solution weaves the technology of Layered Insight—a company acquired by Qualys in 2018—into the broader Qualys ecosystem and gives customers visibility for running containers with protection that is layered into the container image.
I have written about containers and container security for a number of years. I have talked with a variety of container security vendors and discussed strategies for effective container security with experts. There are various approaches to container security, but a container-native solution—protection that is built into the container it is protecting—provides a variety of benefits and advantage that alternative solutions can’t match.
Container Security Challenges
What makes container security during runtime challenging is that the containers themselves are both ephemeral and encrypted. It is not easy to keep tabs on them, especially while they are actively running.
Most container security implementations use techniques that provide some degree of protection but create as many problems as they solve and expose your environment to potential compromise. The two most prevalent approaches to container security are to either use a kernel plugin or privileged security containers. Both of these techniques have issues that make the security solution itself the “Achilles heel” of the whole thing.
A kernel plugin loads a kernel module in the underlying host operating system. The kernel plugin can then monitor calls to containers at the kernel level. To do so, however, the kernel plugin requires access to the host and grants root access by default.
Privileged security containers function in a similar manner but running on the host rather than at the kernel level. A privilege security container requires root access in order to provide visibility into other containers running on the host. Containers are redirected through the privilege security container, which allows it to monitor container activity.
There are two significant issues with these approaches. First, one of the primary benefits of containers is that they modularize applications and make them platform agnostic. However, kernel plugins and privileged containers are both written for specific host operating systems, which locks you into that operating system. It also won’t work on container-as-a-service platforms where there is no underlying host operating system. The other—and arguably larger—problem, is that both require root access, which makes them primary targets for attackers and expose your container environment to risk.
Qualys Container Runtime Security (CRS)
Rather than depending on a kernel plugin or privileged security containers, Qualys CRS integrates an extremely small snippet of Qualys code into the container image itself. This built-in, container-native approach enables policy-driven monitoring, detection, and blocking of container behavior at runtime.
With Qualys CRS instrumented into the container image, the protection will be available anytime the container is running, regardless of where that container is invoked. Qualys CRS provides customers with a viable solution for a variety of sensitive use cases that require stronger security, such as critical file access monitoring and blocking, network micro-segmentation, vulnerability and exploit mitigation, and virtual patching
Build Security into Cloud Workloads
Effective container security extends beyond just runtime, though. Badri Raghunathan explains, “Qualys advocates for a defense in depth container security approach – consisting of scanning the build pipeline, container registries and running containers with its cloud-native container sensor and its unparalleled vulnerability knowledge base. Once the container attack surface is minimized via this scanning approach – a lightweight container friendly runtime security solution can be leveraged to protect the remaining attack surface.”
“Detection and Response in a single application across the container DevOps pipeline is key to effectively secure the containerized applications, as the high-velocity DevOps container pipeline can be exploited by malicious actors at runtime,” said Philippe Courtot, chairman and CEO of Qualys. “Therefore, we must build security into cloud workloads and extend protection into running containers. Qualys brings defense capabilities to our Container Security solution with the addition of policy-driven behavior detection and response capabilities to protect running containers on-premises, in private clouds or in container-as-a-service public clouds.”
CRS is an add-on to Qualys Container Security, and it is available now for Qualys customers.
- Cybersecurity’s Unsung First Responders Step Into the Spotlight - October 16, 2025
- How AI and Integration Are Transforming Software Security - October 13, 2025
- Fighting Machines with Machines: How AI Is Redefining the SOC - October 6, 2025