In technology circles, the acronym SDL is commonly understood to stand for Software Development Lifecycle. There is another very important “S”, though: Security. Intel recently published a white paper that describes the Security Development Lifecycle—an SDL developed to provide a framework for consistent application of privacy and security practices across software, firmware, and hardware.
There are two very important reasons to incorporate security principles and design early and throughout the development lifecycle—cost and efficacy. Security is often not considered until a product is essentially ready for release. At that point, most of the design and engineering decisions are pretty much set in stone and it would be very costly to try to go back and fix security issues that are baked into the core of the product. The alternative is to attempt to address security concerns with band-aids and quick fixes that can hopefully mitigate any issues with less cost, but ultimately are not as secure as fixing them properly.
The Security Development Lifecycle alleviates these problems by ensuring that security is woven throughout the process. A framework for continuous evaluation and improvement is crucial for organizations that have embraced DevOps culture. The accelerated development cadences and automation of builds and deployments demands a security development framework that can keep pace.
Intel has been applying the principles of the Security Development Lifecycle across software, firmware, and hardware for more than a decade. The creation of the Intel Security and Product Assurance organization in 2018 has allowed Intel to further develop and implement security best practices like the SDL. It also supports Intel’s Security First Pledge and the notion that security is an ongoing process rather than just a point-in-time event.
“In today’s dynamic threat landscape, prioritizing security and privacy during product development is critical,” said Vernetta Dorsey, Product Security Practices Enablement Engineer at Intel. “At Intel, we take a holistic approach to customizing the highly integrated nature of hardware, firmware and software development, proactively building best practices into every phase of the security development lifecycle.”
Intel Security Development Lifecycle
There are six key phases of the Security Development Lifecycle:
- Planning and Assessment. Determine security and privacy risks and identify tasks and activities necessary to address them.
- Architecture. Define security objectives and use them to build an appropriate threat model.
- Design. Perform security and privacy analysis based on security objectives, threats, and requirements identified in previous phases.
- Implementation. Perform secure code reviews and static code analysis, and check that architecture and design are performing as intended.
- Security Validation. Employ vulnerability scanning, fuzzing, penetration testing and other methods to ensure product requirements have been met and make “ship / no ship” determination.
- Release and Post Deployment. Conduct testing to ensure previously detected issues have been resolved and continue to scan for vulnerabilities in third-party components and IP. Implement plan to monitor and manage security for the lifespan of the product.
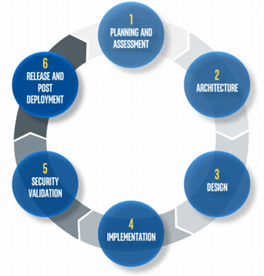
One of the most important elements of the SDL, though, is that it is a continuous circle that repeats and builds on itself rather than a process with a defined beginning and end.
Comprehensive Security Strategy
The Intel SDL is essential for ensuring security, privacy, and consistent quality for Intel products, but it is just one facet of a comprehensive security strategy. Intel also invests in red team exercises, bug bounty programs, hackathons, academic research, and other programs designed to both detect and resolve issues in existing products and raise the bar with new discoveries and innovations for future products.
You can learn more by downloading the Intel Security Development Lifecycle white paper.
- Who Do You Trust Online—And Why? - February 19, 2026
- EC-Council Launches New AI Certifications To Close The Skills Gap - February 10, 2026
- Building Trust into the Cybersecurity Gig Economy - February 5, 2026



Comments are closed.