The online troll world has never been kind to women, especially feminism and women’s rights activists. It’s 2021, yet somehow it feels like we’re still living in 1908. Female bloggers, journalists, and social media activists receive death threats and online harassment with toxic vitriol seemingly reserved exclusively for women.
For example, 73% of female journalists reported online violence and threats in a UNESCO survey. There’s also a number of social issues that are making the waters even more dangerous for women speaking their mind. Radical feminism is now considered “bourgeois Karenism”, and women’s rights groups are accused of misandry, in some way or another.
It’s liberating for women to speak their mind, but so dangerous in the world of online death threats and “cancel culture”. And even when you try to stay anonymous, some people with no lives go playing mystery investigators, prying your details out of the dark. So here is a guide to foolproofing your online anonymity against doxxers and trolls.
Be cautious of free VPN networks
Using a VPN can contribute a little bit to anonymity, but they can also backfire. What VPNs do is send your computer traffic through alternate servers to mask your IP address (very simple explanation). However many of these free VPN servers are hosted by people in garage setups.
Setting up small servers for torrent seeding or contributing to VPN routing is something easily learned in online network and security courses. I always recommend people to try one even if they have no interest in an IT career, simply because you’ll learn so much about keeping yourself safe.
Personally, I’ve known people to use their powers to inspect traffic going through their VPN servers, to figure out the identities of people using VPNs. I’ve also known tech chatroom trolls to do the same thing while working for larger data centers. Overall it is much better to use Tor instead of a free VPN.
Tor also has its own security flaws, but they are very rare and can be mitigated with a little bit of research. You can dig deeper into this such as searching Reddit for “Tor safety tips”, but you will start getting into “darknet” stuff and tinfoil-hat levels of staying anonymous.
Keep personal and throwaway accounts FAR apart
It’s easy to make lapses in judgment while posting anonymously. You might share a personal detail or two, thinking nobody could possibly tie it to your identity. If you examine the tactics used in online doxxing communities (KiwiFarms, 4Chan, etc.), much of it is following tiny trails of clues. People can unbelievably fixate on the tiniest breadcrumb of evidence.
Maintaining an anonymous account from your real identity means never sharing anything remotely personal on the anonymous account. The name of your pets for sure, but even the number of pets you own, for example.
If your social media account shows photos of your 3 cats, and you post on an anonymous forum that you have 3 cats, someone on your trail might find that more than a coincidence. People will comb through every post ever made under an account to find connections.
You very much have to think “How would a private investigator track me down?”, or better yet, invent an entirely new persona and stick to it. For all anyone knows you could be anyone else in the world except yourself.
Another no-no is using the same avatar photo across internet communities. You can easily right-click on someone’s profile image and click “Search Google for image”, which will show you all websites where the same image is found.
Use randomly generated email for signup forms
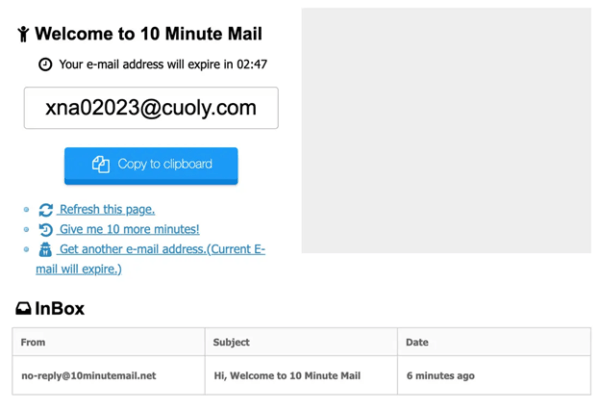
Using the same email, even if it isn’t a personal email, is dangerous when you own several anonymous accounts. Many people keep a “throwaway” email for anonymity but then tie several accounts to it. If that throwaway email is hacked, all of your anonymous accounts are exposed.
A good service is TempMail.org which will give you a totally random, temporary inbox you can use for the exclusive purpose of creating anonymous accounts. You can use it once and then completely forget about it, as most online platforms only ask for email verification one time and then never bother you again.
Use burner phones and prepaid SIM cards

Android phones are very cheap these days, you can find low-spec phones for less than $50 or even second-hand phones. Armed with a few of these, and some prepaid SIM cards, phone verification will be no problem while staying anonymous.
Apps will remember identifying information about your phone model, not just your sim number and IP address. One way is through cache / cookies that get stored on your phone from apps, but there are also ways to get unique serial numbers for the individual parts in your phone.
Use a browser that disables tracking
Popular browsers like Edge, Chrome, Firefox all easily track your online activity and store cookies on your computer. These cookies are unique identifiers. Even if your IP address changes, websites will tie those cookies to your computer specifically.
To completely make your computer appear like a “new visitor” to websites:
- Use a program like CCleaner to completely erase cache/cookies from browsers.
- Manually go into the folders and delete any remaining cache files, like:
“C:\Users\Your User Name\AppData\Roaming\Mozilla\Firefox\Profiles” - Change IP address by unplugging the router for a bit, around 10 minutes should be good enough to force an IP change.
- Open a command prompt and type these commands:
ipconfig /release
ipconfig /renew
ipconfig /flushDNS
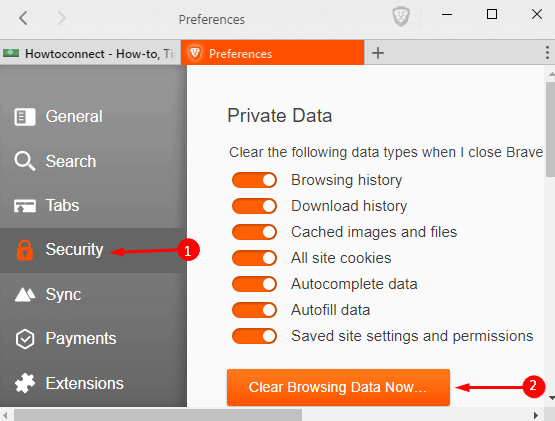
You should also use browsers that disable tracking and automatically delete cookies/cache when the browser is closed. Tor browser and Brave browser are both good for this.
Regularly do account + password security checks
People have a habit of using the same passwords across different accounts and making “easy to remember” passwords like birthdays.
You should have a good, strong password, and then a few variations of this. What do I mean by a “strong password”? Well, that has kind of changed over the years. Bear with me, this is boring info but important to know.
There are 2 common ways that people steal passwords. Social engineering, and brute-forcing.
In social engineering, information is extracted from you that can be used to guess your account security information. I would be kind of very suspicious if someone in a random convo asked me questions like “What is the name of your first pet?”, “What is your mother’s maiden name?”, “What elementary school did you go to?”, etc. But people do not think twice about giving up this info as we love to talk about ourselves!
In brute-forcing, programs are used that will try millions of passwords. It’s like playing every number in the lottery, eventually, you will win! Many years ago, it would take FOREVER to brute force an 8-character password, but CPUs are so fast these days that passwords using dictionary words can be cracked in seconds, minutes, or hours.
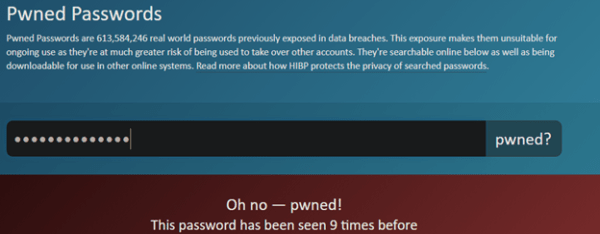
You can also check if any of your accounts or passwords are in any recent data leaks, using a website like HaveIBeenPwned.com – in this screenshot I typed “November111988”.
But let’s try with a password like “FDF42d&^$%vfda^%$fojs%Dsdg#!@#kja”
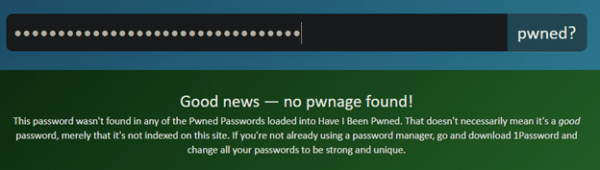
How on earth could you ever remember a password like that? That is when you’ll have to trust password managers and encrypted password vaults.
- A Guide to Staying Safe and Anonymous for Women - June 9, 2021


