Reduce, re-use, recycle.
I guess that mantra also works for malware developers. A new study from CyActive found that many of the biggest malware campaigns of 2014 relied on re-used and recycled components. The question is why are the security solutions we depend on unable to detect and prevent attacks that use exploits and techniques we’ve seen before?
I wrote a blog post about the findings from the report:
2014 was riddled with major data breaches. Retailers, banks and financial institutions, government agencies, and military assets were all victimized by cyber attacks. According to a new report from CyActive titled Cyber Security’s Infamous Five of 2014, though, most of these attacks relied on known malware components that organizations should have been able to detect and avoid.
CyActive found that hundreds of millions of dollars of damage was caused using recycled malware components that have been known for nearly a decade, and that cost very little for attackers to employ. The report focuses on the degree to which these breaches could have been avoided, and the ease with which recycled malware is used to achieve maximum impact. The analysis reveals that the cost and effort required for attacks continues to decline dramatically, while the resources and effort required to detect and prevent the attacks continues to increase sharply.
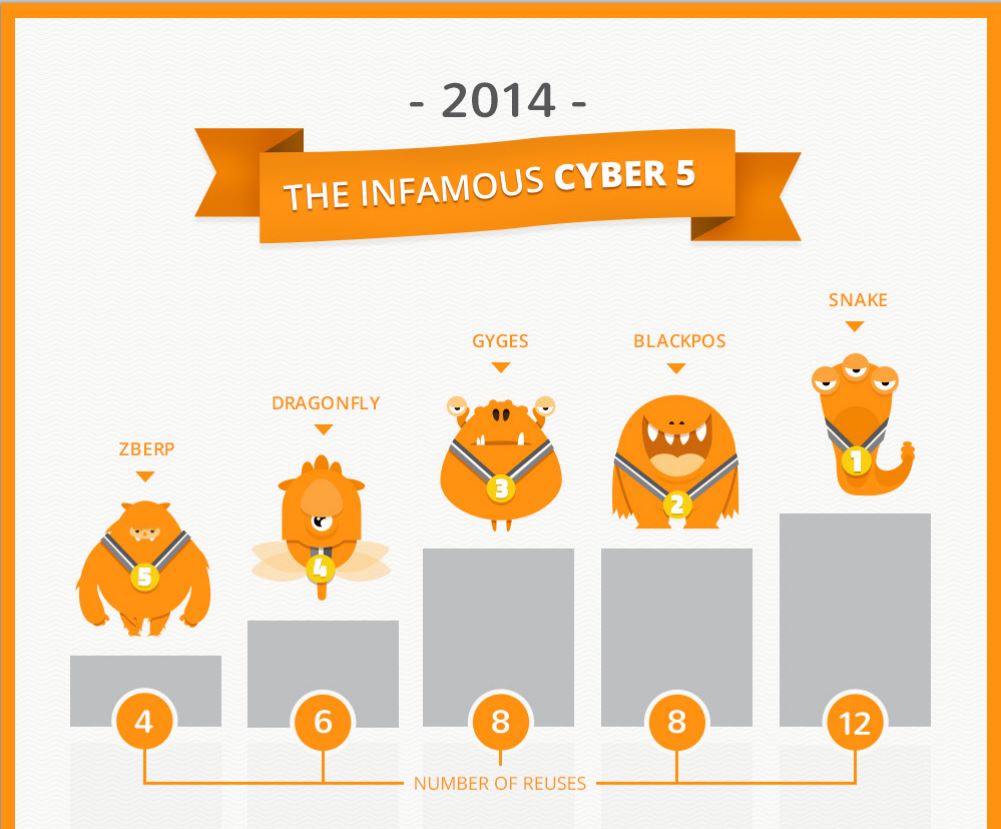
An infographic that accompanies the report highlights the key findings. For example, components from five known malware families were responsible for many of the biggest attacks. Elements of Snake were re-used 12 times and Black PoS caused more than $200 million in damage using eight recycled malware components in a exploit toolkit that can acquired online for as little as $1,800. ZBerp—an attack that utilizes four recycled malware components—hit 450 financial institutions around the world.
The question organizations need to consider is how or why these attacks succeeded. The short answer is that the pervasive model of signature-based detection is flawed and unreliable. Malware developers can continue to use the same attacks and evade detection by signature-based security tools at the same time by simply making a few minor changes to the exploit code.
Read the full post at CSOOnline: Worst cyber attacks of 2014 could (should) have been avoided.
- Exploring the Future of Identity Security and Agentic AI - December 3, 2025
- Tech Gifts Under $30 That Don’t Suck - December 2, 2025
- Smart Holiday Gifting: The Best Tech Under $75 for 2025 - November 26, 2025