Cybersecurity, cyber-terrorism, and cyber defense are serious topics of concern for all industries, government agencies, energy, and national infrastructure entities right now and for the foreseeable future. Securing the information systems, data, and infrastructure of these Governmental, Military, and Commercial assets now is paramount.
What are some of the greatest areas of concern for U.S. IT Security Leaders?
- Security of the National energy grid
- Military drones and micro drone operational security
- Internet of Things (IOT) use and vulnerabilities
The Government and high technology industries must establish or update policies and procedures to help prevent, defend, mitigate, and develop risk based corrective actions to effectively combat these multiple threats. These activities should align with national emergency priorities to prevent or minimize unexpected and unanticipated incidents to high-threat areas related to national security, high technology sectors, and international espionage attempts.
1. The national energy grid and natural resources such as; nuclear energy assets, hydro-electrical generators, water reservoirs, waterways, and oil reserve resource security controls in the U.S. and across the globe must be frequently tested, re-assessed and strengthened.
The security posture and safety of these national and international assets must be carefully inspected, analyzed, and safeguarded to avoid any small or large disruptive event/s that could keep us from maintaining our Government, military assets, national agencies, and local/state entities from performing their planned and unplanned national defense disaster recovery operations.
The Grid Modernization and the Smart Grid whitepaper from the Department of Energy emphasized the importance of grid modernization necessary to bolster and support America’s national security goals, strengthen our global economy, as well as maintaining the health and safety of our population
However, our national electrical grid is outdated and must be upgraded and strictly maintained to keep pace with today’s rapidly growing need and appetite for electrical power to energize the Department of Defense, Department of Homeland Security, high-tech industries, the expanding electric vehicle (EV) revolution, and possibly more hyper-loop transport environments.
Grid Modernization and the Smart Grid also indicated, that the U.S. infrastructure is dated and being stressed beyond its capacity in some instances and in need of critical upgrades. Our infrastructure needs large scale modernization funding that will take advantage of more advanced technologies to provide electricity more reliably and efficiently. These upgrades will also minimize storm power outages and enable faster service restoration after expected and unexpected disruptive natural events. These enhancements will help to energize our companies, military installations, and communities to stabilize their energy needs and advance their current and future backup power strategies.
According to Lila Kee, Chief Product Officer for GlobalSign, there is increased evidence and recent headlines indicating that cyber-attacks against critical systems are on the rise. Cyber criminals have identified national energy infrastructure in general and specifically the electrical grid as potential valued targets for future attacks against the U.S. The Government is now acting to avoid any further delays in energy infrastructure rebuilding and has promised to fortify these national energy assets to protect against future attacks.
According to Recovery Act Reports and Other Materials: SGIG and SGDP Case Studies, indicated that funds have been recently released to start the modernization effort now to renovate our aging energy infrastructure and its overloaded framework. The American Recovery and Reinvestment Act (ARRA) has already invested $4.5 billion dollars in the electric sector, and this amount has been doubled thanks to other private funding to achieve approximately $9.5 billion dollars toward this much needed rebuilding effort. This fast-tracked infrastructure funding will provide America’s key industries, and our businesses a well-deserved advantage so they can reap the benefits sooner from this advanced smart grid project.
Investing in and utilizing nano and micro-grid technologies can enable our military, universities, schools, businesses, and healthcare providers to more effectively support our communities with battery powered backup systems and sub-systems that will work for us during possible natural disasters and catastrophic power outages.
Research conducted by Heather Clancy suggests that the use of microgrids, that are small electrical generating systems can assist our communities, military bases, and companies to provide a reduced cost solution to provide backup and stored power during storms or disruptive events. The U.S. population’s electrical energy needs are estimated to increase almost 75 percent from 1.05 gigawatts (GW) in 2014 to 1.8 GW by December 2017.
The critical need to secure and continuously protect these energy resources is key to our sustained success as a nation and superpower on the global stage. These protection methods and procedures must be designed, tested, and continuously modified to prevent any person/s, groups, or countries from limiting our use of these energy assets today for the future.
2. Our military and commercial sector drone and micro drone research and development programs are essential to enhance our Government’s and military’s goals and missions now and for the next 5-8 years. Global drone research and its uses has become extremely valuable for undersea exploration, airspace surveillance and reconnaissance, and emergency rescue and recovery operations. The future for drones in the commercial and Department of Defense logistics arena is growing rapidly as well.
Research conducted by Divya Joshi in 2017 highlights how over the last three years drones have taken a central position in many of our business capabilities, emergency operations, and military special operations covert and other critical operations. The benefits range from expanding Amazon Prime’s rush-hour deliveries to providing disaster situational awareness footage for response teams and rapid disaster relief for those in desperate need.
These drones are providing a method of reaching, filming, assessing, detecting, and testing environments that may have been too dangerous for humans to reach, or too hazardous to risk sending emergency teams before effective assessments could be formulated and careful plans initiated. Protecting the design, development, operation, security, and control management of these many diverse devices in all industries and agencies is crucial to the increased application and overall future effectiveness of these systems and their dedicated devices.
3. The rapidly growing Internet of Things area poses many cyber security related challenges today for its broad implementations tomorrow. These devices range from vacuum cleaners, refrigerators, lighting systems, heating and air conditioning systems (HVAC), home/business security systems, and other related surveillance systems. Many of these devices and the software to manage these systems are not secured or the security is insufficient to prevent hackers from compromising these devices and systems. Designing, configuring, and securely managing these systems and devices must be carefully analyzed to identify key weaknesses and operational vulnerabilities.
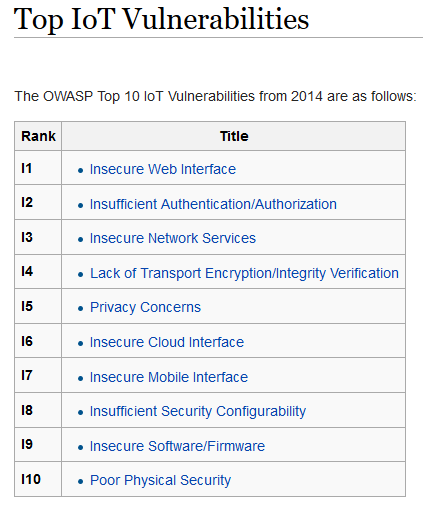
According to OWASP’s Top IoT Vulnerabilities:
The manufacturers, their hardware suppliers/designers, and software developers must be held accountable to use secure coding practices and code signing design procedures to ensure that these systems used to control and manage their devices have a regulated level of security and encryption. This will not only protect their consumer’s personally identifiable information (PII), but also help immensely to secure and safeguard their business partners and supply chain partners intellectual property, sensitive personally identifiable information (SPII) along with their upstream and downstream service providers’ shared data. In the business and Government agency environments due care and due diligence must be practiced and enforced so that these required security related issues will be analyzed, tested, and updated.
A proactive approach is desperately needed to defend against these threats today and will help to mitigate and minimize the negative outcomes that could easily become a dangerous reality tomorrow for the U.S. Government, national security driven agencies, and commercial/defense industries if not properly funded and managed now. These potential defense mechanisms must be put into practice in these areas for robust national security grid protection, reinforced drone and micro drone research, operational/developmental security management, mandatory IOT secure design, development, coding, and secure software development lifecycle best practice implementation.
These security based initiatives are areas of critical importance that must be addressed by our Government, Department of Defense leaders, Department of Homeland Security leaders, and cutting-edge U.S. technology companies striving to achieve or sustain a strong competitive advantage in these industries across the global economy. Protecting these areas of national security interests are essential to protect our natural resources, ensure greater security and stability of our armed forces’ tools, equipment, strategies, and mission success, to enforce regulations, policies, standards, and for securing and promoting growth of the Internet of Things global ecosystems.
- Cybersecurity: What Must be Done Now to Protect the Future? - December 30, 2017



Comments are closed.