Intel is a sponsor of TechSpective
When it comes down to it, money is involved in virtually every form of crime and cybercrime. In many cases, money itself is the primary target, but even when it isn’t, it still plays a vital and central role. Criminals leverage technology to launder and move money—funneling Illicit funds to finance criminal networks, rogue regimes, terrorist activities, and more. Consilient recently launched with a goal to develop a more effective approach to discovering and mitigating financial crime risk.
Consilient was created through a partnership between K2 Integrity and Giant Oak. Gary Shiffman, founder and CEO of Giant Oak and inventor of GOST—a machine learning based screening platform, and Juan Zarate, co-managing partner and Chief Strategy Officer at K2 Integrity, co-founded Consilient to combine deep knowledge of anti-money laundering (AML) and countering of financial terrorism (CFT) knowledge with cutting edge technology, including Intel Software Guard Extensions (Intel SGX), to develop a secure, dynamic, and effective solution to help financial institutions.
Fighting Financial Fraud
Criminal activity within the financial system is a massive global problem. Estimates suggest that between $800 billion and $2 trillion of criminal transactions are moved through financial institutions annually. What is more alarming is that it is also estimated that less than one percent of that activity is intercepted.
An article from McKinsey & Company points out that there has been a rise in technology aimed at helping financial institutions address the problem. However, the article also reveals that as much as 85 percent of financial crimes compliance and anti-money laundering activities are conducted manually.
Consilient’s Zarate declared, “The current global AML/CFT system is an outdated model that requires a new 21st century design that allows financial institutions, authorities, and other regulated actors in the financial system the ability to discover and manage evolving and complicated illicit financing risks to the financial system more proactively, effectively, and efficiently.”
One of the biggest challenges in fighting financial crime is the inability to effectively share information and compare notes between financial institutions. Each company is a silo—an island unto itself. Working in isolation with access to limited information, they have a very limited ability to identify and report suspicious activity. They need to be able to step back and see the larger picture—view larger patterns and connect the dots.
Financial institutions need to overcome these blind spots in order to effectively track sophisticated criminals who are able to exploit weaknesses in the system to obscure their activities. One solution is to encourage organizations to share information and work collectively to identify risks and understand trends. There are significant regulatory constraints and privacy concerns, however, when it comes to sharing sensitive customer and financial data that make such cooperation difficult.
Consilient intends to solve this challenge through the use of Federated Learning with its proprietary DOZER technology. They have created a behavioral-based machine learning-driven governance model. The approach allows its algorithm to access and analyze data from different data sets, financial institutions, and regions without moving the actual data.
Intel SGX and Federated Learning
Consilient overcomes the challenges of organizational silos, and the information-sharing and privacy constraints of traditional AML / CFT systems by building models of what “normal” or “legal” behavior looks like and analyzing activity to identify transactions or patterns that are out of the ordinary.
It is essential to have end-to-end security and privacy safeguards in place to ensure that data remains private and confidential. It is also crucial that the underlying model inside DOZER is protected from theft that could allow attackers to expose data or tamper with the algorithms. To provide these protections and assure the integrity and accuracy of the model, Consilient leverages hardware-based Trusted Execution Environments (TEEs) using Intel SGX.
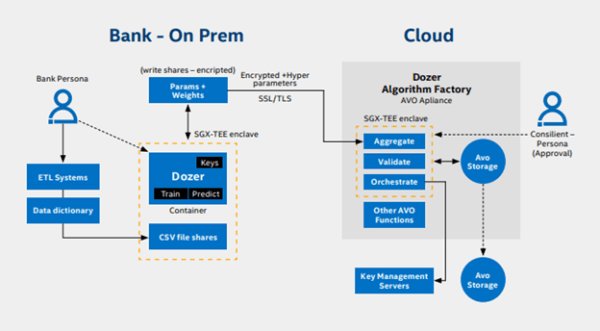
A white paper on the solution, “Federated Learning through Revolutionary Technology,” explains, “Intel Software Guard Extensions is a hardware-based TEE that helps protect against code / data snooping, as well as code and data modifications by malware on the system. The technology has the root of trust limited to a small portion of the CPU hardware and the machine learning application itself. The fundamental principle behind Intel SGX is to minimize the trusted computing base in order to significantly reduce the attack surface from where an attack can be launched.”
Incorporating Intel SGX into the federated learning approach of DOZER enables Consilient to protect against software attacks and attacks against memory content. Data and encryption keys remain protected even in the case of an insider attack or if an attacker is able to gain full control of a target system, and Intel SGX guards against memory bus snooping, memory tampering, and other attacks against contents in RAM. Intel SGX also increases confidence in the integrity of the model and data by providing hardware-based attestation capabilities that allow for valid code and data signatures to be measured and verified.
The Future of AML / CFT Systems
“Identifying and disrupting the financial networks of criminal enterprises is a top priority for our member banks. This promising technology presents new opportunities to more effectively identify illicit financing at the source,” commented Banking Policy Institute President and CEO Greg Baer.
Zarate is presenting a keynote session this week at the ABA / ABA Financial Crimes Enforcement Conference to highlight persistent issues with money laundering and financial crime. He will stress the crucial role of new technologies and the use of machine learning to effectively and efficiently address these challenges.
- Why Data Security Is the Real AI Risk - June 30, 2025
- Why Being Bold Matters in Cybersecurity—and Branding - June 3, 2025
- Gear Tested and Approved: My Top Picks for Dads and Grads This Season - May 28, 2025




Comments are closed.