Organizations of all sizes are facing a serious threat from cyberattacks. As the volume and sophistication of attacks continues to go up every year, there are two significant challenges: their security posture is reactionary, and they lack the resources to react effectively.
Most organizations still rely on outdated, legacy security tools that are ill-equipped to face the threats of today. Traditional security tools like firewalls, anti-malware solutions, and intrusion detection or prevention are still considered to be a staple, more or less, for cybersecurity. However, these tools are primarily signature-based. They give attackers the first shot because detection and blocking the threat first requires the presence of the signature file.
Many organizations also have newer security technologies like SIEM (security information and event management) or SOAR (security orchestration, automation, and response). These tools aggregate threat intelligence and security telemetry to provide a more comprehensive view of the environment. The problem is that they generate a lot of alerts—many false positives if the tool is not properly configured—and responsibility then falls on the IT security team to assess and respond to the alerts. The sheer volume of alerts is overwhelming, and IT security teams are typically stretched too thin to possibly keep up.
More than 60% of attacks today leverage a zero-day exploit, so this reactionary approach is not sufficient. Intrusion developed Shield to address these challenges. Shield takes a more proactive approach to stopping threats—preventing cyberattacks before damage occurs. I decided to take a closer look at Intrusion Shield to see for myself how it works and how effective it is at protecting against attacks.
Form
Intrusion offers Shield as a security-as-a-service (SECaaS) offering. It is a transparent bridge that sits on your network between your edge networking equipment and internal switches and devices. Shield is available in 1GB, 10GB, 40GB, and 100GB trunk versions to ensure maximum throughput and virtually zero latency.
Intrusion sells Shield on a per seat, per month basis. There is no hardware to buy, and no annual contract.
Function
Intrusion Shield does not rely on signature files or wait for attacks to be known. It combines real-time analysis of all incoming and outgoing packets, and AI (artificial intelligence) to detect and kill malicious connections before dangerous traffic can have a negative effect on your network.
Shield also uses a massive database repository of more than 8.4 billion active IP address reputations for IPv4 and IPv6 addresses. The historical information in the database is updated daily based on actual activity from all global devices connected to Intrusion Shield. Shield AI analyzes all the available information to determine a reputation score for the address and kills or allows the traffic connections based on that score.
Basically, Intrusion Shield kills suspicious or malicious connections in real-time. It automatically kills attempted connections if any suspicious activity is detected. Viruses, malware, ransomware, impersonation fraud, IP (intellectual property) theft, business email compromise (BEC), and even fuzzing, contract hacking, and machine learning poisoning are stopped before these attacks reach the dangerous phase of their operation.
Crucial to Shield’s effectiveness, Intrusion Shield monitors outbound traffic as well. If there are already devices in your network compromised by malware, or firewall breaches, or malware in IoT (internet-of-things) devices, Intrusion Shield will block the suspicious traffic generated by those devices as well. Whether it’s communicating with a C2 server for further instructions or malicious downloads, or exfiltrating data, the threat will eventually have to send traffic out of the network—and Intrusion Shield promises to detect and block that activity.
It is a simple solution that works immediately without the need for intensive configuration changes or management. There is no need for an IT security analyst to respond to alerts—it just starts doing its job without generating any alerts.
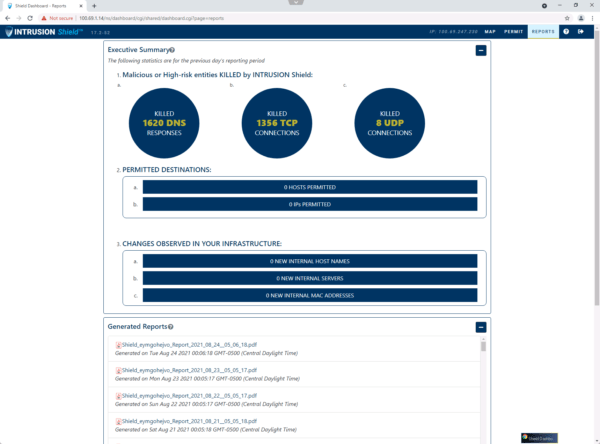
Intrusion Shield provides reporting options so IT managers can maintain transparency with the C-suite and board and demonstrate the efficiency and effectiveness of the protection.
My Experience with Intrusion Shield
OK. Those are the claims made by Intrusion about Shield. The question is, does it work as advertised? Is it really that simple to start blocking threats in real-time? In a nutshell, yes.
It was simple to install, and I was able to be operational relatively quickly. It started doing its job and killing suspicious and malicious connections immediately—and it did so without producing a single alert. However, the daily executive summaries and prioritized mitigation lists look extremely useful as tools to assist IT operators with understanding what is happening and where to focus first.
One of my questions or concerns about Intrusion Shield was whether it would be intrusive and impede my ability to connect to the internet or use the legitimate applications I need in order to do my job. I was worried that there may be false positives, or that the AI might be a tad overzealous and block things like social media platforms or SaaS applications.
I was pleasantly surprised. I did not encounter any such issues while using Intrusion Shield. I went about business as usual—without noticing any lag in network speed or being blocked from any legitimate site or tool.
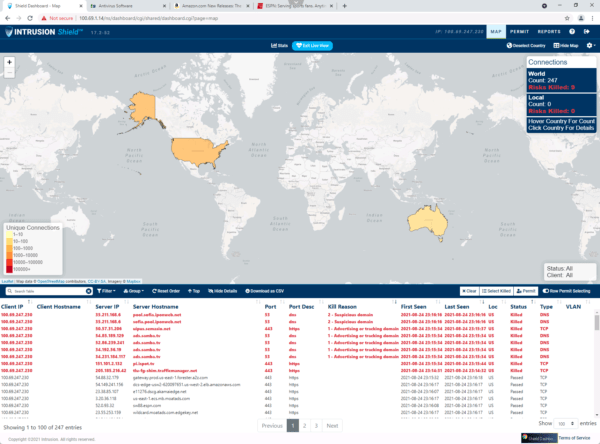
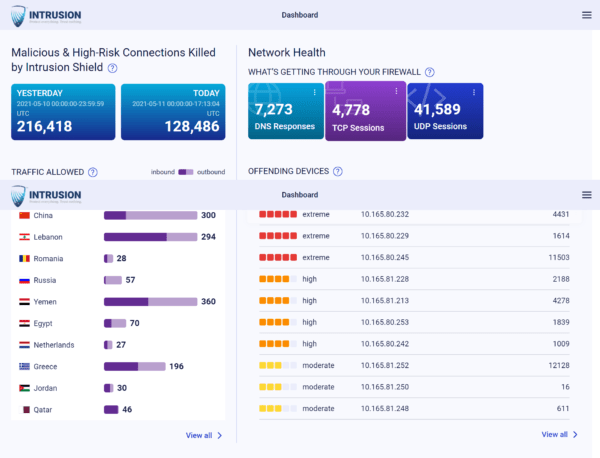
The Dashboard provides an at-a-glance overview of the protection being provided. It displays total killed connections from the current or previous day and a prioritized list of devices that need remediation. A map of the world allows you to view traffic allowed by country, and quickly see where your killed connections are originating from, or just as important, destined to. The darker the color of the country on the map, the more connections there are related to that specific country.
The Dashboard shows the Client IP, Client Hostname, Server (or destination) IP, Server Hostname, Port, Port Description, Direction of Traffic, and Kill Reason—along with data about when it was first or last seen and the country it is in. The Kill Reason field is ranked from 1 to 5—with 5 being the worst. You can click on the Kill Reason to drill down and get more information about why the connection was killed.
As mentioned before, there is a Daily Report that provides an Executive Summary of activity. It provides a simple look at total killed events, permitted destinations, and general observations from the day.
Another question I wanted to answer was, “What happens if Intrusion Shield does kill a connection to a site I actually need to use?”
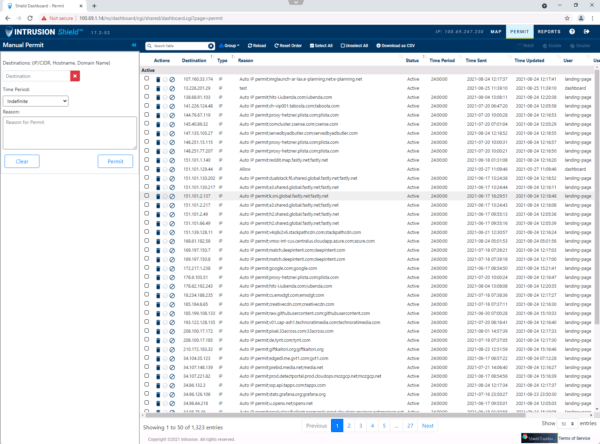
It is relatively simple. I can click on the killed connection and select “Permit All”. That opens a Permit Page—prepopulated with the information from the connection I clicked—and I can choose to allow the connection indefinitely, or I can limit it to a designated period of time, like 15 minutes or 24 hours. There is a field to add a reason for the permit, which may come in handy for future reference. Then you’re done and the IP is added to your whitelist.
I actually did not encounter this issue, though. The AI in Intrusion Shield adds permits to the whitelist automatically as well. It is monitoring and learning and is able to recognize the destination IP addresses that you use often, and Shield learns to permit it.
Overall, my experience was pretty awesome. Intrusion Shield just did what it’s supposed to do—and it did it essentially without me noticing. There was no noticeable latency in my network activity, and there were no alerts to respond to. I just continued using my computer on my local network like I always do, and Shield automatically and proactively killed connections that were suspicious or malicious.
The Verdict
If your enterprise includes many various devices, complex IT architecture and holds valuable corporate and customer/user data, and you want to protect it all against the ever-expanding and increasingly sophisticated threat landscape, I strongly suggest you consider Intrusion Shield.
I am not suggesting that Shield is a “silver bullet” that will magically solve all your cybersecurity challenges. But I am saying that traditional and legacy tools are not equipped to protect against today’s threats, and that Intrusion Shield is an affordable, intuitive solution that will immediately and automatically move your security posture from reactive to proactive, and significantly improve your cyber defenses while moving you toward a zero-trust environment at the network level.
You owe it to yourself to at least check it out and maybe request a demo to see what it can do for you.
- Why Data Security Is the Real AI Risk - June 30, 2025
- Why Being Bold Matters in Cybersecurity—and Branding - June 3, 2025
- Gear Tested and Approved: My Top Picks for Dads and Grads This Season - May 28, 2025




Comments are closed.