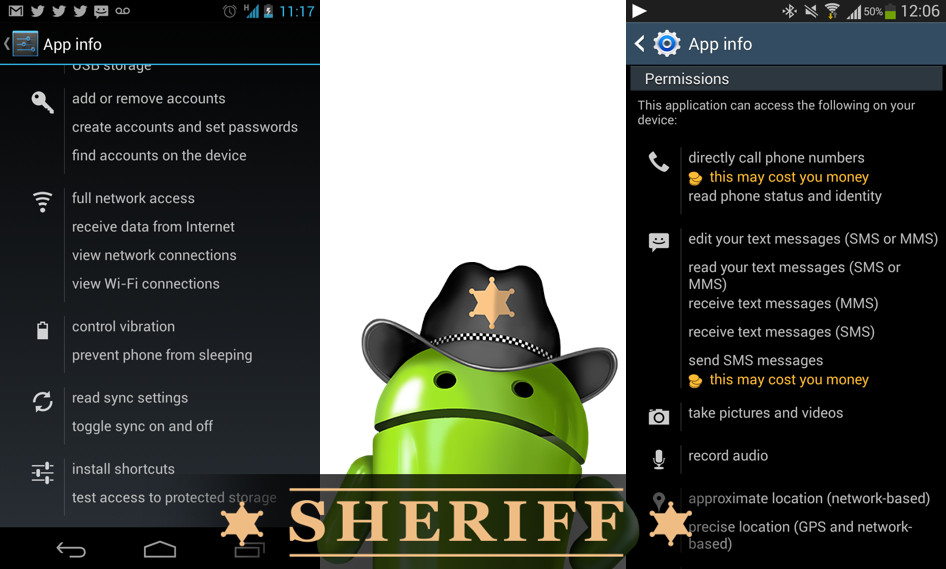
Malicious apps are out in the wild, but some have even snuck by the official scanners in Google and Amazon stores on Android. And with apps requiring more and more permissions for seemingly straightforward tasks, it can sometimes fall on the user to see if the app itself is doing what it is advertising.
Policing your apps by merely inspecting permissions can be a difficult game. On the left we have Facebook, and on the right we have Facebook messenger. With apps that are as full featured as Facebook, Facebook messenger, other messenger apps, or other telephony apps, you will often see a large daunting list of permissions like this. Even legit camera or flashlight apps might request scary permissions simply to use your camera, mic, or LED flash for their intended, benign purpose.This illustrates how difficult it can be to play sheriff, merely using permissions, to know if something is going to be malicious or not.
Bouncer & “Verify Apps”
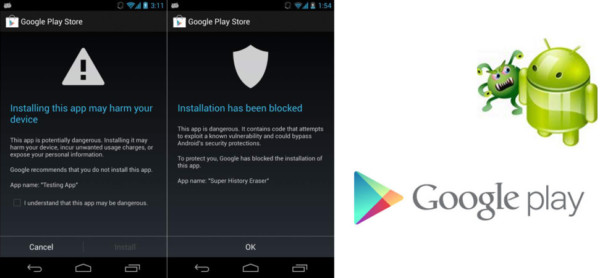
Luckily in the case of known malware, we have Bouncer and Verify Apps to help us out. Bouncer is Google’s method of scanning apps on the Play store for malware. This includes being scanned as they’re submitted or updated, as well as scanning past submissions. On actual user’s devices, the updated version of “Verify Apps” will also perform routine checks even after an app is installed, whether or not it even came from the Play store. Such checks have various triggers, such as perceived harmful or risky actions – like requesting root access.
Google says the tool will also do a periodic scan every few days or so. These are Google’s current solutions to scanning for and protecting users from malware on their phones. Unfortunately, it has been proven in the past that neither solution is foolproof, and there are ways around Bouncer and the Verify Apps scans. Bouncer has overlooked fairly obvious malicious activity in the past, however. A great example of this would be the handful of popular Play apps which contained hidden cryptocurrency miners found some time ago.
Adware

As a user who sticks only to Google play, eats all his vegetables, and drinks all his milk may still run into apps which are not necessarily malware, but still have a negative impact on their device or experience. We consider these apps to be various types of adware and potentially unwanted applications (PUAs), whereas Google sometimes agrees and sometimes does not. On the left, we see one known as Android.Airpush. This adware will inundate your phone with push notifications like an email or Facebook notifications, but instead are just poorly conceived advertisements. Various advertisers, including the original Airpush have made steps to become more legitimate and inform users of their actions before installing on a device. Due to this some have been able to come out of PUA status and provide a better experience for their advertisements.
To the right, we see one of the more relatively recent adware discoveries in the play store, an adware which would falsely advertise issues with users’ devices in full screen pop ups after unlocking the device. This app would sometimes wait WEEKS to reveal its true colors, because of this time gap it becomes more difficult for the user to determine exactly which app caused the problem. To be specific in the code it instructs to wait for x reboots or y days to create confusion around what recently installed app might be the culprit. Upon clicking some of these advertisements, users could be instructed to install other various malicious 3rd party applications.
Fake Apps
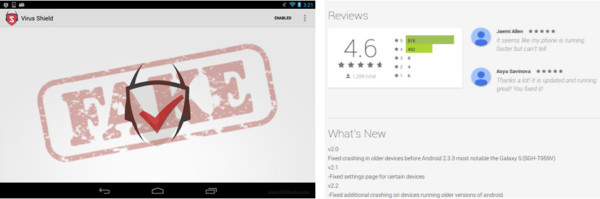
Another big story of not-really-malware in the play store was “Virus Shield”. Virus Shield is an app that claimed to be a light weight anti-malware application at the low cost of $3.99. Unfortunately, for those that bought the app, it did LITERALLY NOTHING other than put some nicely rendered pictures on your screen. What it WAS able to achieve was an exceptionally high review score possibly aided by fake reviews. It was able to achieve over 10,000 purchases, becoming the top paid app on the play store that week before finally being found out and removed. Fortunately, those which purchased the fraudulent app were refunded.
Banking Malware
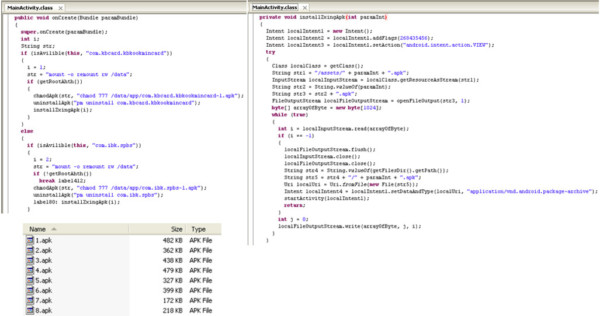
Another type of malware we’ve seen outside Play, somewhat frequently, is banking malware. Fake banking apps are made, in most cases, to look like their real counterparts to trick users into entering their sensitive bank information. Once they have the information they want, they send it off to the bad guys. Here we see a couple different shots of the code from a sample of Android.Bankun, as well as a list of apk files from within that app. On the left, the code shows how this app goes through a list of “if else” statements to search for banking apps already installed on the phone. You can see the beginning of this list, and therefore the first two apps it’s looking for.
Once it finds an app it’s looking for, this malicious code then checks for and, if available, uses root permission to go mount the phone’s app storage so it can be read and written to, add permissions to the already-installed app so anyone can read, write, and execute it, and then uninstall the found original app. Lastly, it installs its own replacement version from the list of files pictured. On the right side we see the installation code, where it loads the corresponding file, based on which “if else” statement was successful, and installs it. This basically just uses a simple counter from the “if else” list to determine which file is needed.
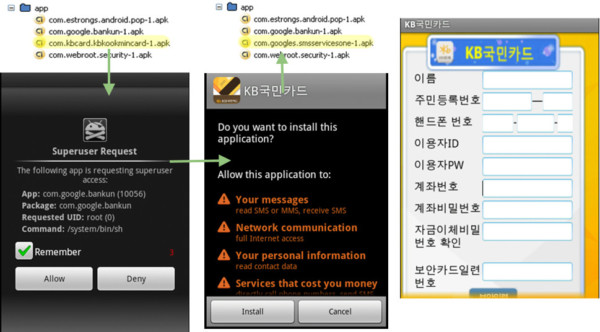
In this case, we installed the first app it was looking for to watch the malware and see how it does what it does from the user’s point of view, which we see here. If you look in the Google Play market you’ll see that “com.kbcard.kbkookmincard” is an app called “KB Kookmin Card Mobile Home”. It appears to be a Korean banking app. In the upper-left corner, you see the legitimate banking app installed on the phone. Next, there’s the app getting root access. Now, the average user capable of rooting their phone would probably be seeing lots of red flags by now and click ‘Deny’, but that’s no fun.
If you click allow, the app will do what we saw on the last slide. It will uninstall the existing app and up comes an installation for the malicious replacement. You can see the shot of the installer and then the end result of the malicious app now having replaced the original. Upon running your “updated” app, it will then ask for all the information it wants to steal, likely in the same style as the original, or close to it. This is very similar to most kinds of phishing out there where imagery and trademarks are “spoofed” or reused to appear more legitimate to increase the chances of fooling users into inputting sensitive info.
While the app store is not perfect, there are protections in place, and paying attention to not only the apps permissions but who is distributing it can help keep mobile users safe. While some have gotten through the scans, luckily feature rich security solutions like Webroot will keep the users safe from scams, strange permissions, and fake apps.
Part 2: Mobile threats: Drive by downloads – Android.Koler
Part 4: Mobile threats: Premium SMS malware
- Mobile threats: Remote access Trojans (RATs) - July 7, 2015
- Mobile threats: Premium SMS malware - July 6, 2015
- Mobile threats: Google Play – Malware from the store - July 3, 2015