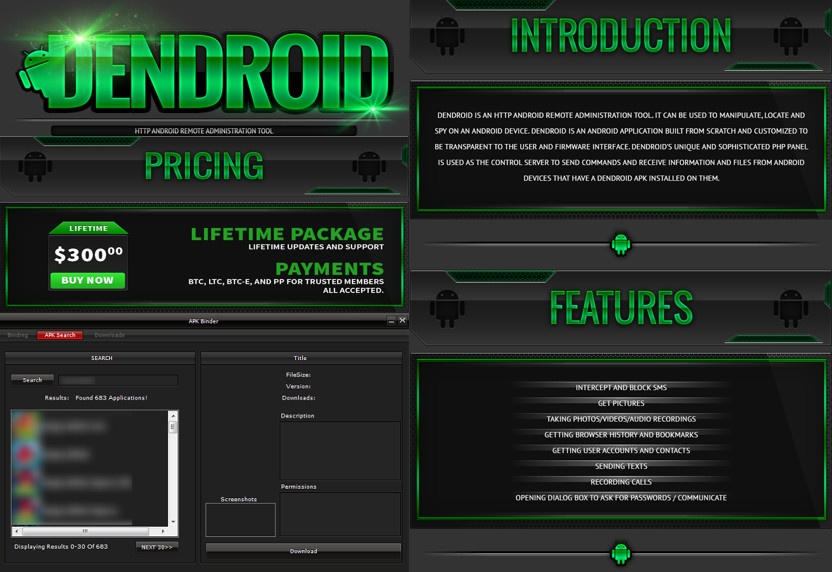
Another malware that seems to be relatively popular due to convenience are Remote Access Trojans. A few have surfaced on Android, sharing many of the same “sold as a package”-type deals you would see with their PC counterparts. Dendroid is a great example of this. Here we see a nice, big advertisement for this malware package and its large array of features. You simply buy the package from the original author and use the tools provided to create your own, infected versions of any app searchable within the tool, which is likely using Google Play as its source.
The screenshot above is of the actual tool. In the lower-left shows a user searching for Angry Birds and getting a list of applications they can choose to repackage with the malicious code. Once you have the malicious app, you would redistribute it as you please, but you would not be able to upload it back to Google Play without being the original developer of that app or changing the app further, namely the package name. It is possible that someone might pick a lesser-known developer or app to modify and then re-upload that infected app after gaining access to the developer’s account. This leaves users to question whether any 3rd party versions of these apps outside the Play store may contain malicious code, like that added by the Dendroid tool.
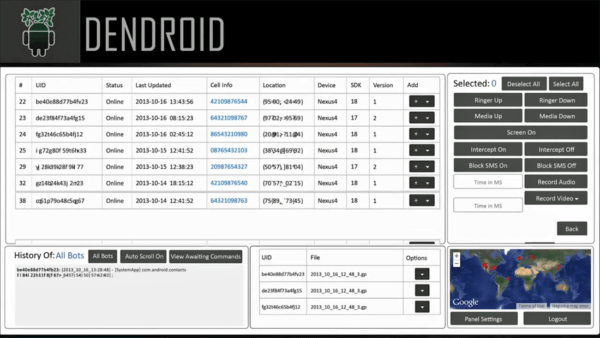
Here’s just a follow up image to show what the buyer would expect to see once he has tricked users into downloading and installing his “special” version of whatever app he chose. As the ad stated, a nice web-based interface for controlling the devices shows a handful of functions the bad guy can force the phones to do, as well as information about each infected device. He can change volumes of the ringer or media, turn the screen on, intercept and block SMS, and record audio and video. Each device shows information like the type of device, version of the OS, and even GPS location.
Being one of the more malicious and invasive of the security threats seen in the wild, it is also one of the rarer ones to see get on protected phones. Often, the devices will need to be jailbroken or rooted, and the user downloading from less than savory app stores. But that is not to say awareness is not necessary as it is possible someone would be able to hack in and submit an ‘update’ to a legit app from the developer’s account. Watching the updated permissions during these downloads, as well as having an updated, full security suite such as that from Webroot, will keep users protected.
Part 4: Mobile threats: Premium SMS malware
- Mobile threats: Remote access Trojans (RATs) - July 7, 2015
- Mobile threats: Premium SMS malware - July 6, 2015
- Mobile threats: Google Play – Malware from the store - July 3, 2015