It’s a well-established fact that companies prefer cloud solutions to on-premises ones when it comes to practically any software. It’s estimated that over 80% of all enterprise workloads will be in the cloud by 2020. But what about an intranet? Are they steadily moving into the cloud too? Definitely, yes.
There are many reasons for companies to adopt a cloud intranet. Enterprises can eliminate expenses associated with a cumbersome and technically complex on-premises infrastructure, reduce intranet customization and support budgets, as well as ensure the performance that can outshine the one of an on-premises solution.
Indeed, the providers of cloud solutions, such as Amazon Web Services, often boast a 99,99% uptime for their services. So, even if your intranet goes down, you can assume that it will be up shortly after. That’s not always the case with on-premises intranets, especially when you suffer from a hardware issue, which can’t be resolved easily.
However, along with multiple benefits, cloud intranets still bring many concerns, security being the most critical one. Almost 70% of enterprises cite security as the main roadblock on their way to the cloud. And there are multiple examples that only reinforce these fears.
We all still remember the infamous iCloud hack with millions of accounts directly breached by hackers, exposing personal data. The Tesla cloud account hack exposed telemetry and vehicle servicing data, as well as allowed hackers to use the account itself for cryptocurrency mining.
At the same time, it should be noted that the cloud security problem is often exaggerated. It’s important to remember that a lot of the horror stories about cloud breaches aren’t indicative of cloud security overall. It’s evident that the human factor plays an important role in cloud security, while technology-specific hacks are rarer.
Strengthening the Cloud Intranet Defenses
So how can you make your cloud intranet impregnable? There are many ways to do that, and here are some of them.
Multi-Factor Authentication (MFA)
Creating proper authentication procedures for your intranet can make a huge difference for your security. For example, Office 365 offers multi-step verification options to end users. This means that on top of providing their account credentials, users may be required to verify their account via a phone call, a text message, a notification, or a verification code sent to a specified phone number.
Authentication on Mobile Devices
Your employees will definitely need to access the intranet using their smartphones or tablets. This provides another opportunity to set up a secure perimeter. As suggested by SharePoint consultants from Iflexion, the Microsoft Authenticator app can be used as one of the verification steps to request an action from the user, like providing their fingerprint.
Password Policies
One of the often-overlooked security best practices is a strict password policy. Many collaboration platforms offer password policy enforcement, like Atlassian Access that lets you define secure password combinations and their expiration rules.
Auditing
Maintaining a detailed activity log for your intranet allows you to identify potentially suspicious activity while meeting regulatory requirements (HIPAA, PCI DSS, SOX, etc.) that require companies to protect customer data they work with. For example, audit log reports in SharePoint Online allow administrators to track various user activities across the intranet, including item views, downloads, and shares, changes applied to intranet content, and more.
Log auditing is available in all well-known intranet products, like Confluence. They allow companies to identify bad actors within the company or compromised user accounts. Irregular download patterns, unusual search requests, or other suspicious activities can be a red flag, indicating that a user takes illegitimate actions or unknowingly lost control over their account.
DLP Policies
Data Loss Prevention (DLP) policies and tools ensure that you minimize security risks related to sensitive data management.
SharePoint Online offers a robust DLP suite that allows you to control how files and data are treated under certain circumstances (block file sharing, encryption of shared files, etc.).
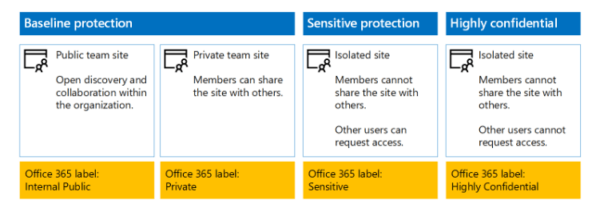
You have to be strategic about the way you set up your DLP policies. It’s a meticulous process, but your security will only benefit from it. Platforms like SharePoint Online do have automated or semi-automated tools to perform the DLP policy setup.
Advanced Security Measures
All the above-mentioned security controls are must-haves for any cloud intranet, and they don’t require much implementation effort. At the same time, if your organization needs to follow a stricter security strategy, it’s worth thinking about integrating your intranet with professional security solutions.
There are plenty of robust third-party monitoring suites as well as security processes that allow you to have a better visibility into all the activities within a corporate intranet, thus providing you with comprehensive security data for timely decision-making. Among possible solutions are Security Information and Event Management (SIEM), User Behavior Analytics (UBA), and Identity and Access Management (IAM).
Recruiting Experts
It’s vital to maintain the security of your intranet, and that’s why it can be not enough for you to rely solely on internal resources to set up a comprehensive security infrastructure. It’s reasonable to involve external partners who can help you scope the range of security features and protocols required to establish an airtight perimeter around your intranet.
Multi-Layered Protection Is a Must
Cloud intranets are very popular today because they offer multiple collaboration features coupled with simplified management and support capabilities. However, the growing adoption of these solutions doesn’t mean that they are immune to security risks, especially if we take into consideration the fact that many of those risks are driven by the human factor.
That’s why organizations should take up full control and responsibility for the security of their cloud-based intranets. It should be said, though, that you can’t be overly concerned about the infrastructure that you don’t fully control. Still, you have to ensure that your solution is used in line with the established security standards.
A multi-layered defensive approach to intranet security in the cloud may include, among other measures, ongoing user activity tracking and content control. Your security protection can also extend to implementing enterprise-level security analytics tools as well as advanced authentication and biometric access control when it comes to mobile solutions.
- A No-Compromise Approach to Your Cloud-Based Intranet Security - September 16, 2019




Comments are closed.