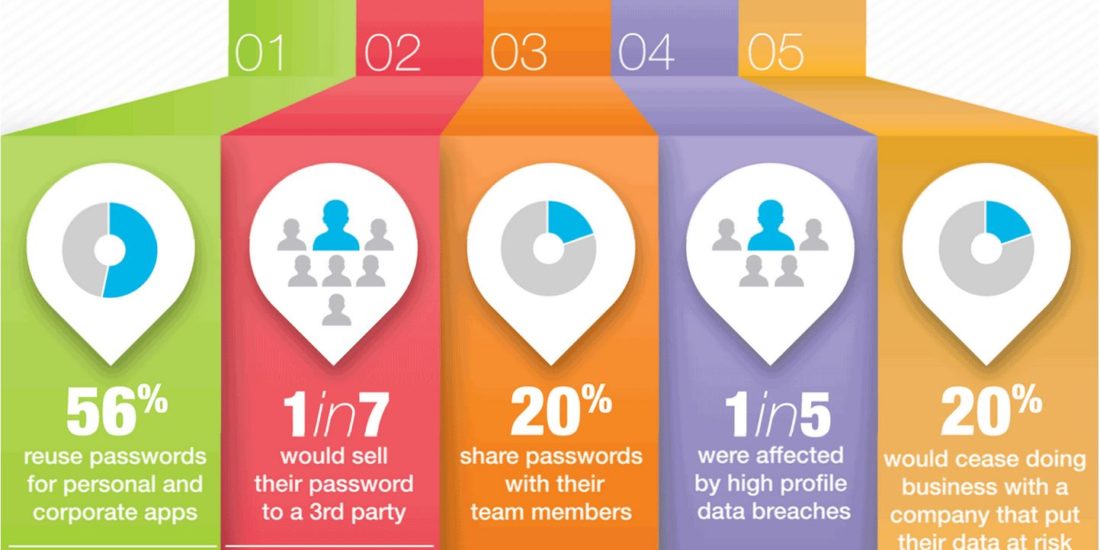
Tighten security with risk-based authentication
It has been proven repeatedly that passwords alone are a weak form of authentication. Two-factor authentication adds an element of complexity that makes it more secure, but also much less convenient. The solution may lie in risk-based authentication—an authentication mechanism […]
Tighten security with risk-based authentication Read More »